Table of Contents
Have you ever wondered what mysteries are still unsolved? Some codes and ciphers have stayed unbroken for centuries and are considered ancient. Since the start of sending messages, people have hidden their secrets. The main trick was to avoid eavesdropping while messengers quickly and quietly delivered the messages. The key to the most famous codes and ciphers in history was simply to avoid getting caught, which connects them all.
To avoid being discovered, ancient codes and ciphers were made with great care and precision. And, we are going to discuss them here in this blog which is curated by the experts of AllAssigmenthelp. But before we begin, make sure you understand what the difference between a code and a cipher is.
What Are Codes And Ciphers?
In a code, every word in a message is changed to a code word or symbol; in a cipher, every letter is changed to a cipher letter or symbol. Indeed, ciphers are what most people mean when they say “code.” Through decoding and deciphering procedures, ancient writings and languages have been comprehended; the most well-known example is the Rosetta Stone of ancient Egypt.
Since the topic of this blog is codes and ciphers, we will only be giving a brief introduction to them here. You may get in-depth explanations of everything from experts by getting online assignment help if you’d like to learn more about them.
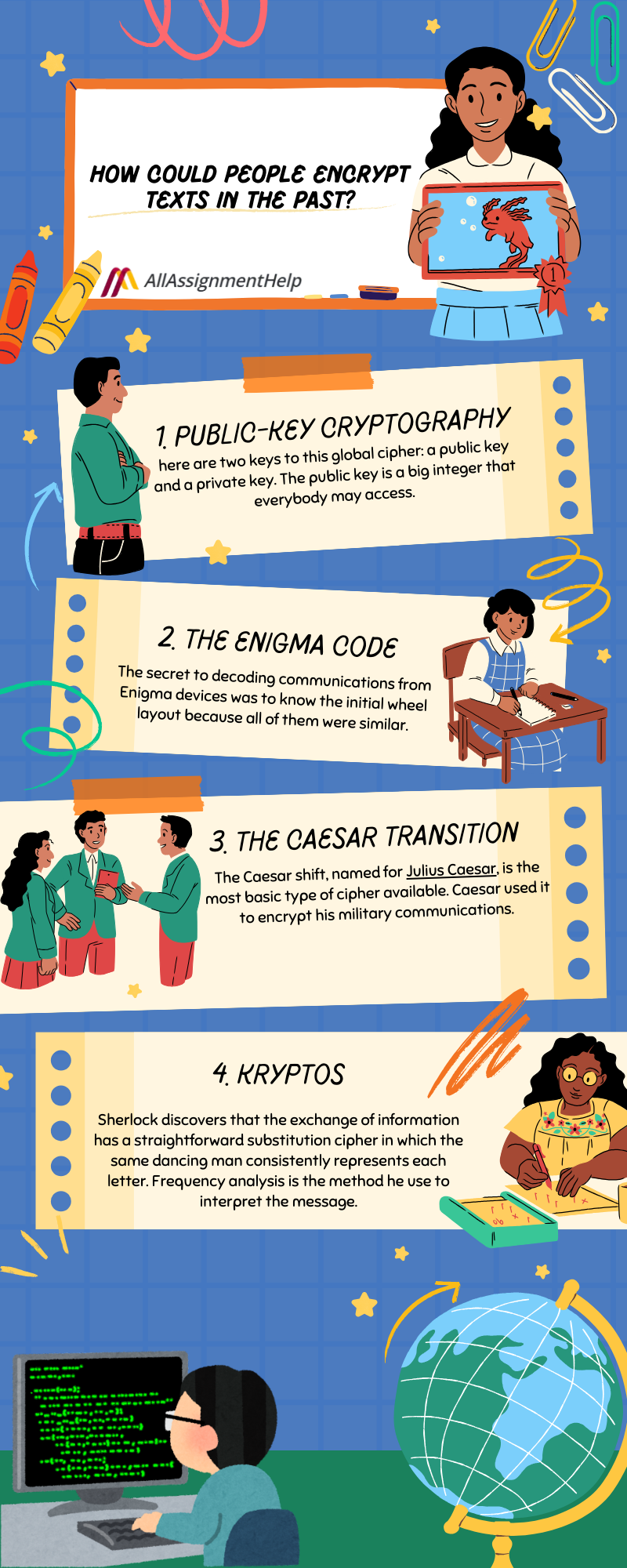
How Could People Encrypt Texts In The Past?
Ciphers have been used for thousands of years to keep those secrets safe from strangers in a game of cat and mouse between code-makers and code-breakers. Text encrypting techniques are as varied as our creative ideas. But there are very few real-world uses for any one encryption technique. Both sides must be aware of the encryption and decryption techniques, which also need to be sufficiently strict to prevent outsiders from figuring them out.
Though there are dozens of different kinds of hidden messages, we will only briefly examine a few in this article:
1. Public-Key Cryptography
This is one of the most secure ciphers available today, and it comes in different forms. It works with two keys: a public key and a private key. The public key is a large number that anyone can access. While messages can be encrypted using the public key, they can only be decrypted with the private key.
For example, when you send personal information to a bank or use your bank card at a machine, the data is encrypted. Only the bank, using its private key, can unlock and read the information.
2. The Enigma Code
During World War II, the Germans used an advanced cipher called the Enigma code. It relied on the Enigma machine, which resembled a typewriter. When a key was pressed, the corresponding encrypted letter would light up on a display. Deciphering Enigma-encrypted messages required knowing the machine’s initial wheel configuration, as all machines followed a similar setup. Adding to the complexity, the cipher constantly changed within a message since the wheels rotated after a set number of characters were typed.
3. The Caesar transition
The Caesar shift, named for Julius Caesar, is the most basic type of cipher available. Caesar used it to encrypt his military communications. All you need to do is move each letter of the alphabet by a certain number of letters to the right or left. Although we can crack this code in our sleep now, it took 800 years for ancient codebreakers to figure out how to do it, and nearly another 800 years to develop a more sophisticated method.
4. Kryptos
During 1990, the CIA installed a sculpture on the grounds of its Langley headquarters that featured a complicated four-part code, teasing its own analysts. Only three of the four components have been solved thus far.
5. Sherlock’s code
Sherlock discovers that the exchange of information has a straightforward substitution cipher in which the same dancing man consistently represents each letter. Frequency analysis is the method he use to interpret the message.
If you are a history student who is interested in learning more about the Sherlock Code, you can use an assignment help service. There are competent historians who are extremely knowledgeable in the areas they specialize in. They will give you accurate data on the subject you request.
6. Skytale Cipher
Scytales, often spelled skytales, originated in Ancient Greek cryptography. This device used a transposition cipher, where a parchment strip was wrapped around a cylinder to encode messages. It is said that the Spartans and other ancient Greeks used this cipher for secure communication during military battles.
To read the message, the recipient wraps the paper around a rod with the same diameter. Its advantages include speed and error resistance, which are important qualities in a combat zone. It is easily breakable, though.
7. Pigpen Cipher
The pigpen cipher is a geometric simple substitution cipher, which exchanges letters for symbols which are fragments of a grid. The example key shows one way the letters can be assigned to the grid.
The cipher is believed to be an ancient cipher and is said to have originated with the Hebrew rabbis. Thompson writes that, “there is evidence that suggests that the Knights Templar utilized a pig-pen cipher” during the Christian Crusades.
Parrangan & Parrangan write that an individual, possibly a Mason, used it in the 16th century to save his personal notes.
In 1531 Cornelius Agrippa described an early form of the Rosicrucian cipher, which he attributes to an existing Jewish Kabbalistic tradition. “The Kabbalah of the Nine Chambers,” as later authors termed this system, employed the Hebrew alphabet instead of the Latin alphabet. It was utilized for religious symbolism rather than any discernible cryptological purpose.
You can get help with this pigpen cipher even though we think you understand it; if you have a history homework pending due to this particular topic as it is hard nut to crack. In such cases, we would like to suggest, you can get history homework help. The historians will assist you in completing homework.
8. Morse Code
Morse code is one of history’s most famous codes and ciphers. It is a telecommunication method that encodes text characters into standardized sequences of short and long signals, known as dots and dashes (or dits and dahs). Named after Samuel Morse, one of the inventors of the telegraph, Morse code remains a significant part of communication history.
The International Morse Code represents the 26 English letters (A–Z), some non-English letters, Arabic numerals, and a limited set of punctuation and procedural signals (prosigns). There is no distinction between uppercase and lowercase letters. Each symbol consists of a sequence of dots and dashes, with the dot duration serving as the fundamental unit of time measurement in transmission.
Does Morse code fascinate you? Do you want to deepen your expertise in this unique form of communication? In the past, learning Morse code was a challenging task, requiring extensive practice and dedication. However, with today’s technological advancements, mastering Morse code has become more accessible.
Students can now seek online class help from experts worldwide, making it easier to learn and apply this historic yet relevant coding system. Whether for personal interest, professional growth, or historical appreciation, online resources provide the support needed to excel in Morse code.
9. The Voynich Manuscript
The Voynich Manuscript is a text with illustrations written in an unidentified script and language. Wilfrid Voynich, an Italian antique book merchant, came up with this enigmatic paper in 1912.
Many researchers have attempted to decrypt the document throughout the years, but they have not been able to make any headway. A sequence of dots and dashes forms each Morse code symbol.
The language and substance of the Voynich Manuscript remain a mystery to scientists, linguists, and cryptologists alike.
10. The RSA encryption method
For the majority of human history, both the coder and the decoder were required to use the same key for ciphers. However, Massachusetts Institute of Technology researchers discovered a means to securely encrypt messages without disclosing the key in advance in the 1970s.
Public-key cryptography protects the majority of modern electronic communications. Cracking it may or may not happen, but if it were possible, you would own almost everything on the internet!
These were the most well-known ciphers and codes that everyone ought to be aware of. We have a number of other posts that might be of interest to you if you are a history student or a person who loves to know about the past.
Conclusion
From ancient methods like the Caesar shift to modern techniques such as public-key cryptography, these encryption tools have evolved to meet the ever-growing need for privacy. While some, like the Enigma code, once seemed unbreakable, advancements in cryptography have continuously challenged and refined our ability to decode hidden messages.
Learning new coding languages has always been an exciting activity. However, with busy academic schedules, it can sometimes be overwhelming for students to manage online exams, classes, and assignments. In such situations, don’t hesitate to seek online assistance by connecting with our experts. Simply reach out to us and say, take my online exam for me, and we’ll handle the rest!
FAQs
| What makes the Great Cipher so well-known? It is among the most well-known codes and ciphers in recorded history. The Great Cipher earned its moniker due to its exceptional quality and perceived indestructibility. |
| In WWII, what kind of ciphers were used? Almost all cipher systems in history, including the Caesar and Atbash ciphers, and the electromechanical machines used in World War II belonged to this logical class. |