Table of Contents
Think of a world in which your face, fingerprint, voice, or any other physical characteristic takes you to another world, the digital world. The future of security lies not just in your knowledge, but also in who you are. We call it the world of biometric authentication. Moreover, we are revolutionizing online identification with biometric authentication, a digital identity solution that leverages our distinct physiological and behavioural characteristics to provide safe and easy access to private data, devices, and services. Hence, this blog by All Assignment Help will take you on a trip from the fundamentals of biometric authentication to its broad world. So, let us learn how biometric authentication has changed lives.
What is Biometric Authentication?
Using distinctive biological traits like fingerprints, faces, voices, or other biometric identifiers, biometric authentication is a type of data security that allows people to be uniquely identified. Moreover, access to devices, safe networks, computers, databases, buildings, and much more may be provided via authenticators.
Biometric authentication may significantly boost a business’s security requirements for shared device scenarios in order to preserve a safe digital workspace. Moreover, there is an added sense of comfort at work since access to firm systems is restricted based on an employee’s physical characteristics. These days, security encompasses not just what you know (password), but also who you are (biometrics).
But like any other security system or password, biometric authentication techniques may be cracked. Thus, this is by no means a flawless setup. Therefore, to keep your business safe, it’s critical to stay up to date on the newest technological advancements and biometric data.
Also read: How to Effectively Manage Your Online Humanities Class?
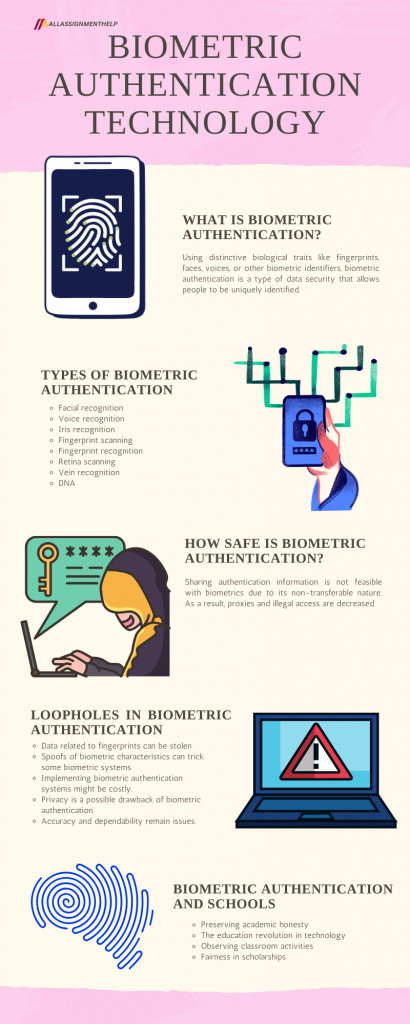
Types of Biometric Authentication
Given below are some majorly known types of biometric authentication.
Facial recognition
Using a camera to scan your face and compare it to a picture, facial recognition technology confirms your identity. Moreover, to make a faceprint, algorithms measure, evaluate, and map the characteristics of the face as well as the space between them. Furthermore, this faceprint is not an image, but rather a lengthy, distinct string of digits, similar to the ID card number but considerably longer.
Voice recognition
Voice recognition examines the user’s vocal quality. The length of the vocal tract and the anatomy of the nose, mouth, and larynx determine each person’s distinctive voice. Moreover, the user’s speech analysis is a powerful authentication method because of all these characteristics.
Iris recognition
The distinctive patterns observed in the eye may be used for both recognition and identification. Also, retinal analysis equipment is costly, which makes it less widely used. Furthermore, iris patterns can be changed by conditions like cataracts. You can learn more about cataracts and other information related to eyes and iris recognition through physics classes. The topics can be complex sometimes but you can always get through it easily with the help of experts. Moreover, if there are topics that are giving you a tough time and you are wondering, if can I pay someone to take my online class, then yes, you definitely can. An expert will take your class on your behalf and will help you understand everything in an easy manner. So, what are you waiting for? Let’s make the best use of the technology.
Fingerprint scanning
This technique may be used as multi-factor authentication for an extra security layer or as a single biometric identification. The term “flat” fingerprint biometrics refers to biometrics that are typically obtained by pressing the fingers of the subject against scanning equipment. If the register is completed in person, verifying someone’s identification using this approach is rather simple. However, a great deal of work is being done to create transformational technologies that can safely translate this fingerprint recognition data such that they are compatible with flat registries that already exist.
Fingerprint recognition
To confirm an individual’s identification, fingerprint recognition uses that individual’s distinct fingerprint. This biometric authentication method is the most widely used since it can be used to safeguard anything from cars to buildings to mobile devices.
Retina scanning
Visible blood vessel patterns are created when a strong light is directed towards the eye in retina scanners. The authorized pattern stored in the database is compared with these patterns after they are read by the scanner.
Vein recognition
Vein pattern identification is of three types. These are palm, finger, and retinal vein recognition.
Since each person’s vein pattern is different, you may use the vein pattern as a security and identification tool by using reference points stored in the pattern. Moreover, the vein pattern is recorded as an image in the majority of vein pattern recognition systems, and it might or might not be encrypted.
Similar to palm vein pattern recognition, finger vein pattern recognition operates on the same concept. Due to deoxygenated haemoglobin, the vein pattern in the fingers may be detected by shining near-infrared light on it.
Retinal vein pattern recognition uses a non-infrared laser beam to scan the retina through the eye. Moreover, this light is absorbed by the retinal blood vessels, which allows for the recognition and storage of the vein pattern as an image. Retinal vein pattern recognition is becoming less and less used, mostly due to its lack of simplicity of use.
DNA
The process of confirming someone’s identification using their distinct DNA profile is known as DNA authentication. To verify a person’s identification, a reference sample and a sample of the person’s DNA are compared.
Also read: What Contributes to the Popularity of Online Literature Classes Among Students?
How Safe is Biometric Authentication?
A user can save more time using biometric authentication than with conventional authentication. Moreover, the inconvenience of carrying access cards and memorizing multiple passwords for various systems has also become less. You may not even need to authenticate yourself in some situations when behavioural biometrics, like gait, are used. Furthermore, sharing authentication information is not feasible with biometrics due to its non-transferable nature. As a result, proxies and illegal access are decreased.
You must have seen people’s voices, faces, and fingerprints imitated in a number of films. Despite its seemingly, being only in the movies, it can actually occur in the real world. However, access to a person’s biometrics and a high level of expertise are required. Hence, we can say, that biometric spoofing is highly challenging.
Loopholes in Biometric Authentication
Biometric systems are not a perfect means of identification or authentication, even if they are getting more efficient as technology develops. Below is a list of some of the biometric systems’ loopholes.
Data related to fingerprints can be stolen
Fingerprint attendance systems frequently keep information on physical characteristics in a local database, including fingerprint and palm veins. This data is associated with certain employees. Sometimes, it is imperative to keep the data secure. Businesses that use fingerprint attendance systems must take precautions to guard against data theft or hacking.
Forgery
Exact duplicates or spoofs of biometric characteristics, such as fingerprints or facial features, can trick some biometric systems. Moreover, to get beyond some biometric security measures, this can be a picture, a three-dimensional model, or a silicone fingerprint duplicate. Hence, it is crucial to use cutting-edge biometric technology, which can detect even the most complex deep fakes.
High cost
Implementing biometric authentication systems might be costly. Both the technology itself and the expense of installation and updates can be quite expensive. Moreover, it can also be a labour-intensive process for trained staff to record each user’s biometric information throughout the system enrollment process.
Whilst high costs might worry businesses, you do not have to worry about the high costs of online assignment help services to meet your academic needs. As a student, if you ever find yourself facing academic problems, you can hire an expert online without worrying much about the prices as there are several affordable assignment writing services for your assistance.
Privacy issues
Privacy is a possible drawback of biometric authentication. Moreover, the idea that a third party, like an employer or government agency, would retain their biometric data worries a lot of individuals. Furthermore, this data may be susceptible to cyberattacks and other security lapses, which means it might be misused.
Shortcomings in authentication methods
Despite recent major advancements in technology, accuracy and dependability remain issues, particularly when improper calibration or maintenance is applied to the system. Additionally, ageing and sickness can cause changes over time in specific physical traits including features, irises, and fingerprints. This implies that access problems might arise if the system does not constantly identify the user.
The requirements of your company and your financial situation will ultimately determine whether or not to use biometric authentication. If used properly, technology may add an extra degree of protection and convenience, even if it can be costly and invasive. Furthermore, considering biometric authentication might be worthwhile if your company wants to update its access control system.
Biometric Authentication and Schools
Let us read how biometric authentication has taken its place in the educational sector.
Preserving academic honesty
Regretfully, during exams, hackers or even students themselves may be able to use cybersecurity flaws to change scores or get access to unapproved materials. Moreover, this is true for students who learn online since it might lead to unethical behaviour when an instructor is not physically there. Biometric scanners can lessen the severity of this issue by verifying users’ identities and stopping them from accessing records without authorization or lying on tests. Furthermore, they are frequently seen at testing facilities, but many online courses demand that students have a camera in order to watch them while taking tests, this is known as webcam proctoring.
The education revolution in technology
It is now more crucial than ever for educational institutions to maintain security. The government in different countries has also recognized the necessity of putting in place a biometric attendance system at colleges and schools in order to reduce the practice of missing classes and increase technological sophistication. Also, allowing students to identify themselves using biometrics is a terrific method to provide ease and security on campus. In addition to this, the internet is also a great reform in education. Hence, you can use it to solve any academic hurdles you come through. For example, if you are unable to complete your assignment with accuracy and authenticity then you can ask an online coursework service to assist you with the same.
Observing classroom activities
In addition to monitoring the courses in which most students participate, this solution may also be used to detect abnormalities in body posture during tests, provide prompt medical attention to the student or instructor, and even identify instances of students giving chits to their friends in order to help them. Students would eventually gain independence and develop into mature, future-focused individuals.
Assessments
Biometric research minimizes cheating and security lapses while assisting teachers in carrying out their lesson plans. Additionally, biometrics helps with identity verification for online learners by using facial recognition capabilities. Moreover, for students who are unable to relocate in order to complete their academic degrees, it also offers an inexpensive substitute. It is possible to verify equal opportunity by identifying the learner’s identity many times during the exam with the appropriate software.
Fairness in scholarships
Scholarship programs across the globe have made significant progress in streamlining the payout process with the use of biometric authentication. A novel method to guarantee worthy students receive their scholarship money without difficulty is the procedure. Moreover, this technology improves security and removes possible inconsistencies by including biometric data, such as fingerprints and face recognition.
Conclusion
In every field, biometric authentication has become widely used. It has several uses that improve user security and convenience. Moreover, older biometric solutions’ problems have been removed by the more advanced technologies. The most widely used biometric technology in the majority of facilities will be face recognition. Moreover, contactless fingerprints or palm recognition are also used. Furthermore, hotel and hospitality, travel, law and order, healthcare, border control, public distribution, and other businesses may all benefit from its many uses.
Frequently Asked Questions
| Question: What makes biometric authentication so important? Answer: When a user accesses a physical space or account, systems retain the biometric data so they can immediately confirm the user’s identity. Since each person’s fingerprints are distinctive, biometric authentication is typically more secure than conventional authentication techniques. |
| Question: For scholarships, what does biometric authentication mean? Answer: By preventing the possibility of a single person submitting several applications, biometric authentication guarantees fairness for all candidates. Moreover, this technology ensures that scholarships are given to the worthiest applicants on the basis of merit. |